Have you ever wondered what lurks inside the master telephone socket that eircom provide? Surprisingly little, as it turns out. Here is a photo of the insides of one of them:-
(click on the photo above for a bigger version)
The circuit diagram of the master socket is:-

There are two sets of three connectors. The connectors are labelled L1, L2 and R. Each connector is directly connected to its counterpart on the other side via a breakable link on the circuit board. The breakable links are tracks on the circuit board which run between pairs of oblong holes (visible in the photo above on the far right-hand side). I think the idea is that two lines could be delivered via the same socket by breaking these links (although I have never seen or heard of this being done). The (two-wire) eircom line is connected to L1 and L2. L1 from the left-hand side connects directly to pin 6 on the RJ11 socket and via the breakable link to pin 4 in the RJ11 socket. Similarly, L2 from the left-hand side connects directly to pin 1 on the RJ11 socket and via another breakable link to ping 3 in the RJ11 socket. Since pretty much all modern telephones only connect to pins 3 and 4 of the RJ11 socket, this is really all you need. For historical reasons, there is a 1.8uF capacitor connecting L1 on the left-hand side to the R pin on the left-hand side. This is connected to pin 2 directly (and pin 5 via another breakable link) on the RJ11 socket. This provides a separate ringing signal for (old) phones that need it.
Apart from the capacitor, the only other component on the circuit board is a 470K resistor. Between R and L2. This (in series with the capacitor) provides a load which eircom can use to test the line remotely when there is nothing else connected (even at a few tens of Hertz, the impedance of the resistor will dominate that of the capacitor).
I had expected to find some sort of surge arrestor or something like that in there but there isn't one (the equivalent BT master socket has a surge arrestor, but is otherwise identical internally - although obviously the socket is physically different).
Practically speaking, you can ignore the R pin completely...I think pretty much all modern telephones will derive their own ringing signal from the line and don't rely on it being delivered separately from the master socket. So the only significant connections in the master socket are these:-

The idea is that the eircom line will connect to L1 and L2 on the left-hand side (I think these are labelled S1 and S2 in newer sockets) and you will connect your own internal wiring to L1 and L2 on the right-hand side. Then, in the event of a fault, it is easy to isolate your internal wiring from the bit eircom are responsible for (thus avoiding a costly call-out charge if you haul out and eircom engineer to a fault which turns out to be with your internal wiring !).
There are stories told of old modems which require you to snip everything except pings 3 and 4. I have only come across it twice in my long and distinguished career fiddling with such things. I can't claim to have a clear understanding of exactly why this is (sometimes) necessary...I have been offered several conflicting explanations. I think it is to do with some (cheap and nasty) modems shorting some pins together internally. If anyone would care to volunteer an explanation I will update this article accordingly.

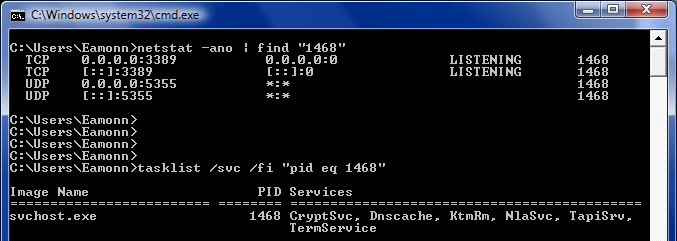
 Imagine my dismay when my new, fast-everything-dual-core-with-tons-of-RAM PC suddenly started running at around 50% CPU utilisation more-or-less constantly, even when it wasn't supposed to be doing anything. You just don't have these problems with Linux ;-) . Anyway so began the detective-work.
Imagine my dismay when my new, fast-everything-dual-core-with-tons-of-RAM PC suddenly started running at around 50% CPU utilisation more-or-less constantly, even when it wasn't supposed to be doing anything. You just don't have these problems with Linux ;-) . Anyway so began the detective-work.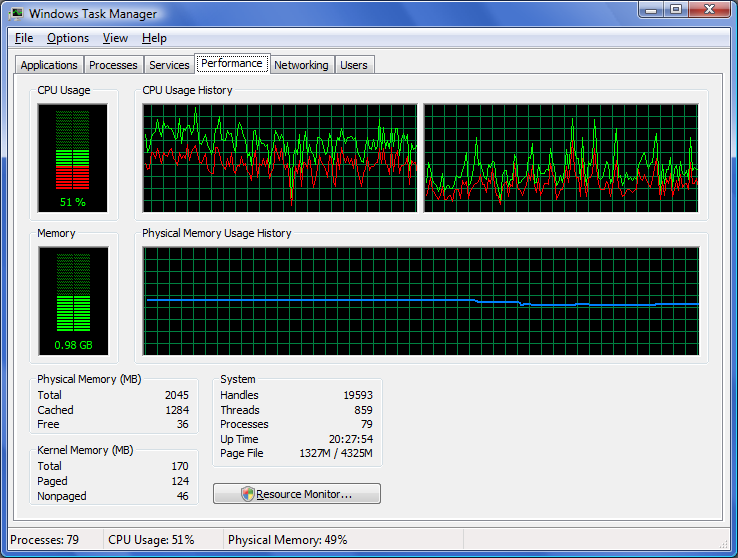

















 SCART pinout (female connector seen from the front). Image is taken from Wikipedia.
SCART pinout (female connector seen from the front). Image is taken from Wikipedia.